Last month, my company allowed me to claim some benefits through a dedicated platform. This platform is specifically built for this purpose and allows you to recover these benefits not only in the form of coupons or discount codes, but also as reimbursements for medical visits or interest on mortgage payments.
I wanted to try the latter.
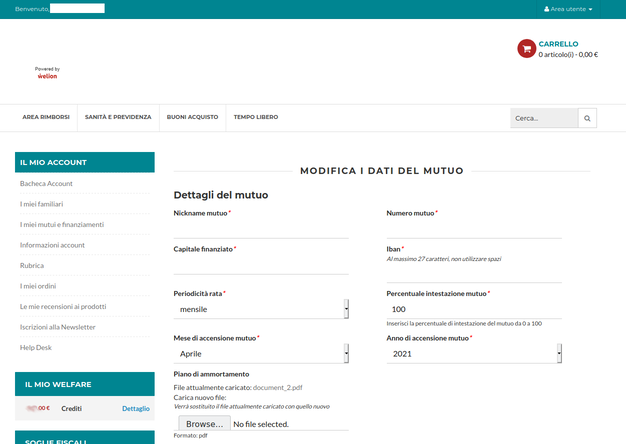
I logged on to the platform and then I filled in all the (many) details about the loan that the plaform asks you to fill in, until I had to upload my amortisation schedule which contains a lot of sensitive data. In fact, a strange thing happened at this step: my file was named document.pdf, but after uploading it was renamed to document_2.pdf.
How do I know? Well, let’s have a look to the UI:
It clearly shows the file name and that’s also a hyperlink. Let’s click then.
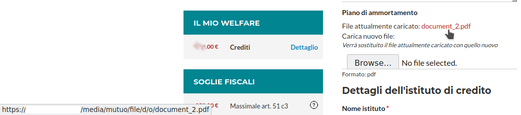
The PDF opens in my browser. This is expected, but what happens if we take the URL and try to open it in a private window?? Guess what?
You guessed it.
Let’s have a look to the URL again. It’s in the form: https://<host>/media/mutuo/file/d/o/document_2.pdf.
That’s tempting, isn’t?
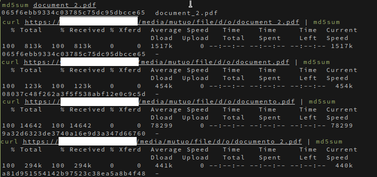
I wanted to have some fun and I tried the following:
Both the curl output and the checksums are enough to understand that some document has been downloaded there (but discarded since I didn’t download them to my disk…).
Thus, since the d and o parent folders match the two initial letters of my file, I successfully tried with stuff like:
/c/o/contratto.pdf,/c/o/contratto_2.pdf, …/c/o/contract.pdf, …/p/r/prospetto.pdf, …
and it does also work with numbers too (to find this out I had to upload a file named 1.pdf 😇), e.g. https://<host>/media/mutuo/file/1/_/1_10.pdf.
Conclusion
If you have uploaded your amortisation schedule to this platform, that in its website says it has more than 300k users from 3k different companies, well someone may have downloaded it.
I reported this privacy flaw to the CSIRT Italia via a PGP encrypted email; the CSIRT is supposed to write to the company that owns the platform to alert them to the problem, but a week later I still hadn’t heard from either of them. So after a week I pinged the CSIRT again, and they replied with a plain text email telling me that they had opened an internal ticket and were nice enough to embed my initial PGP encrypted email.
Two weeks later (about 21 days since my first mail) the platform fixed the problem (the uploaded file path isn’t deterministic anymore and authentication is in place), but I still haven’t heard from them.
Addendum
Since <host> is a third-level domain in my case, I used stuff like Sublist3r and Amass, but you can also use the online version hosted on nmmapper.com, to perform DNS enumeration and I found ~50 websites, 30 of which are aliases pointing to the same host. In fact, I could replace <host> with each of them and I would always download my document_2.pdf file.
Tags: coordinated vulnerability disclosure, security, privacy